The development of quantum computers poses a threat to the security of the cryptographic algorithms currently in use. Quantum computers have the potential to solve certain mathematical problems, on which many cryptographic algorithms are based, much faster than conventional computers. This means that the security of encryption methods based on these algorithms can be reduced and even broken through the use of quantum computers. This development also has an impact on security-relevant areas in automotive electronics: At a time when connected vehicles and autonomous driving are becoming increasingly important, the integration of post-quantum cryptography is becoming a decisive factor for the security of vehicle communication. In an interview with AEEmobility, Continental experts Maurice Heymann (Applied Cryptography Researcher) and Dr. Sheikh Mahbub Habib (Head of Cybersecurity and Privacy Innovation) provide information on where we stand, how big the threat is and what measures need to be taken today.
AEEmobility: What is the current status of quantum computers?

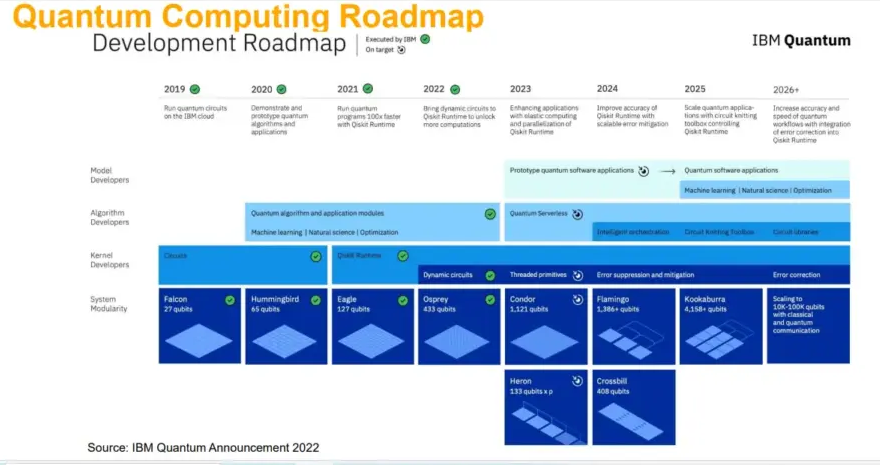
Maurice Heymann: In research, IBM is one of the leaders in the development of quantum computers. The roadmap (see image below) clearly shows the state of the art. IBM started with 27 qubits in 2019, but the number has increased exponentially over the years. As things stand today, these qubits are still subject to errors. Although such deviations are not relevant for applications such as AI and machine learning, these errors are fatal for cryptography.
Therefore, in practice, you combine, for example, a thousand of these qubits with errors and generate an error-free qubit from them. However, this in turn means that if, for example, a thousand qubits are needed to break the cryptographic process, a thousand times a thousand qubits are required. We have not yet come that far.
Due to the fact that the performance of quantum computers is increasing almost exponentially, the US National Institute of Standards and Technology (NIST) called on companies and research institutes back in 2016 to develop procedures and algorithms to protect encryption processes from quantum computers. The NIST has now selected an algorithm developed by IBM called Kyber (FIPS-203) and is in the process of standardizing it. The final version of the standard is due to be published this year. Three algorithms are expected to be standardized for digital signatures (Dilithium (FIPS-204), FALCON (tbd) and SPHINCS+ (FIPS-205). Further algorithms are being evaluated to cover various use cases and underlying mathematical problems.
Which encryption methods are threatened by quantum computing?
In cryptography, two different methods are generally used to encrypt or sign data: symmetric and asymmetric methods. Asymmetric cryptographic systems are based on a private and a public key and are referred to as public-key methods. Asymmetric methods are mainly used in vehicle electronics to establish communication channels, for car-to-cloud services, software-over-the-air updates, secure boot, etc.
With symmetric encryption, both parties have the same key, which must be exchanged secretly. However, the public-key method is also used here to pass on this key. It can be assumed that symmetric methods can be adapted relatively easily and are then considered quantum-safe. Asymmetric encryption methods such as RSA or ECC, on the other hand, must be replaced by quantum-resistant algorithms.
When is there a threat to current encryption methods? And when should post-quantum protection be implemented?

Dr. Sheikh Mahbub Habib: A survey by Dr. Michele Mosca and Dr. Marco Piani from the Global Risk Institute is very helpful in this regard. Every year, they ask experts from research and industry when they expect a suitably powerful quantum computer to arrive and how they are preparing for it (picture below). The results show that there is a 50 percent probability that quantum computers will break current encryption and signatures from around 2035.
In relation to the automotive market, this means that with a development time of 1 to 3 years and a vehicle service life of approx. 10 years, the topic is highly topical – in fact, it is already too late. It is therefore important to invest in this area now, because if you miss the point, it will be very costly.
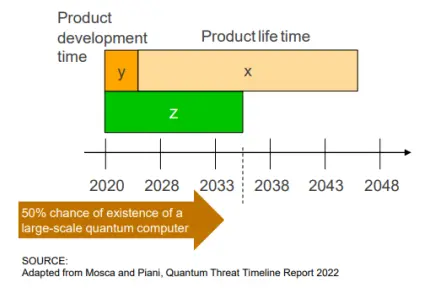
Quantum Threat Timeline Report 2022: Experts call Q-Day the day when quantum computers will be available that can crack asymmetric cryptographic methods such as RSA. (Image: Mosca and Piani)
What specific measures do you propose?
The scientific consensus is to replace classic asymmetric methods such as RSA and ECC with quantum-resistant algorithms. And for symmetric algorithms such as AES, the security level should be increased by doubling the key length to 256 bits.
Is the automotive sector leading the way here and how are other industries reacting to this threat?
Maurice Heymann: Some companies are already starting to integrate post-quantum secure cryptography into their products. This is particularly important in industries where long-term security and trust is crucial, such as finance and healthcare, but also in the automotive industry. Google has already converted its entire internal production network to post-quantum secure algorithms – in a hybrid process. This means that traditional, tried-and-tested algorithms have been combined with future-proof post-quantum cryptography, thus creating a second level of security: if one method fails, at least the other is still available. Furthermore, the system was designed to be crypto-agile, which means that the systems have a modular structure to enable easy updating and expansion of the encryption functions. Individual components and encryption algorithms can therefore be replaced independently of each other without affecting the entire system. This allows new algorithms and encryption techniques to be integrated while older, less secure components are removed or updated. Crypto-agility is therefore also an important topic for us from an architectural point of view. Otherwise, each control unit would have to be upgraded and tested individually.
Google has also already made the Chrome browser post-quantum secure on the end user side (Chromium Blog: Protecting Chrome Traffic with Hybrid Kyber KEM). This means that any data that is exchanged with a server that supports this is already post-quantum secure.
And where is Continental on this issue?
Dr. Sheikh Mahbub Habib: There are many technical challenges to overcome before PQC technology can be used in vehicles in general. As part of the BMBF project QuantumRISC, we worked with other companies and research institutions to investigate various topics in the field of quantum security with regard to embedded hardware. To this end, we identified typical use cases at Continental together with our subsidiary Elektrobit and developed our own AUTOSAR Classic Library, which contains various post-quantum algorithms. These were implemented in a client-server system and then benchmarked in terms of memory space and speed. From this, we were then able to derive the requirements for the embedded hardware in the vehicle, as it is well known that automotive electronics in particular do not have unlimited computing power and memory available. And there are currently no hardware accelerators for post-quantum algorithms on the market for automotive-specific applications. However, with the publication of the draft standards by NIST this year, it is to be expected that hardware support will also be provided by semiconductor manufacturers.
Maurice Heymann: In terms of use cases, we focus on ECU software updates, secure vehicle diagnostics and secure communication channels, which are also used for applications such as Car2X. We used the algorithms Kyber for encryption and Dilithium for signatures, which ran on a 32-bit AURIX TriCore microcontroller TC38x from Infineon. In comparison to pre-quantum algorithms, we found enormous differences in speed and the consumption of memory resources. It is interesting to note that the dilithium algorithm runs almost three times faster than the pre-quantum algorithm RSA, but requires almost five times as much RAM and 50 percent more ROM. For encryption, the Kyber algorithm is even 10 times faster than the traditional X25519 algorithm, but requires twice as much memory for RAM and ROM. This means that the memory hardware requirements increase significantly when using PQC algorithms. We are currently working on optimizing this problem, for example reducing memory requirements at the expense of speed.
Why is it necessary to adapt post-quantum algorithms to automotive requirements?
Dr Sheikh Mahbub Habib: The algorithms that are standardized by NIST were developed for the IT industry and still need to be optimized for automotive applications. There is no such thing as a „one size fits all“ algorithm. For us, this means that we have to select the optimum algorithm for each use case. There is also the issue of crypto-agility, which is not easy to implement in the automotive sector due to the processes, hardware limitations, performance and security aspects. In the worst-case scenario, the hardware would have to be replaced in the event of a software update. The migration of post-quantum technologies to automotive is certainly not trivial; we are still at the pre-development stage.
Continental and Elektrobit have joined forces with several partners to investigate how automotive devices can be protected from threats posed by (sophisticated) quantum computers. The aim is to select suitable algorithms for the automotive market that are suitable for common use cases:
- Secure download of a software update from the Internet
- Establishing a secure channel for communication with other devices in the vehicle and with the outside world
- Ensuring authorization of access to/from the vehicle by end users and other parties (e.g. V2X communication)
These use cases were implemented in the PQC demonstrator and evaluated in terms of calculation and communication time. The results are integrated into the Elektrobit AutoSAR crypto stack and enable OEMs and suppliers to secure the vehicle inventory or components in advance against the threat of quantum computing on cryptographic algorithms.
Is there a cross-industry initiative or does each manufacturer develop its own?
Maurice Heymann: There is currently no cross-manufacturer collaboration. AUTOSAR could possibly set up a working group. Some manufacturers have at least announced that they will support post-quantum cryptography in future vehicle architectures. We at Continental will be holding a number of workshops with our customers this year. We are also working with semiconductor manufacturers such as Infineon and NXP on SoC-based hardware accelerators and are contributing our experience. Our subsidiaries Elektrobit and Argus Cyber Security are also working intensively on this topic.
What is your conclusion, what measures do you recommend?
We have gained extensive experience through our project work. We advocate dealing with this topic as quickly as possible, as the day when quantum computers break traditional algorithms is highly likely to come.
The migration to post-quantum cryptography (PQC) is not easy in the automotive sector, as there is no „one-size-fits-all“ solution and a lot of optimization effort is required. Depending on the use case, PQC algorithms can be faster than pre-quantum algorithms, but tend to require more hardware resources (ROM & RAM). Hybrid solutions are preferred by us to offer the future-proofing of PQC algorithms combined with the traditional security of tried and tested algorithms. However, it must be said that even with a complete migration to PQC, there is still a residual risk. It’s ultimately a cat-and-mouse game, with mathematicians and developers proposing new algorithms and others trying to break them. (oe)
Thank you very much for the interview!
(The interview was conducted by Klaus Oertel, Editor-in-Chief of AEEmobility)